MEMBUAT JARINGAN VPN SEDERHANA MENGGUNAKAN CISCO PACKET TRACER
SETTING SERVER
1. Buatlah topologi seperti gambar dibawah ini.

2. Dari gambar topologi kita menggunakan 1 server,2 router dengan tipe 1841,1 switch dengan tipe 2950-24,2 PC.
3. Klik server pilih config kemudian setting gantikan display name nya (terserah anda) kemudian isikan gateway nya setelah itu pilih FastEthernet0 kemudian isi IP dan Subnetmask.


4. Masih pada server pilih service pilih DHCP dan AAA kemudian kita setting.


SETTING ROUTER
Untuk R1 VPN SERVER
router>en
router#conf t
router(config)#hostname R1
R1(config)#aaa new-model
R1(config)#aaa authentication login VPNAUTH group radius local
R1(config)#aaa authorization network VPNAUTH local
R1(config)#crypto isakmp policy 10
R1(config-isakmp)#encr aes 256
R1(config-isakmp)#authentication pre-share
R1(config-isakmp)#group 2
R1(config-isakmp)#exit
R1(config)#crypto isakmp client configuration group ciscogroup
R1(config-isakmp-group)#key ciscogroup
R1(config-isakmp-group)#pool VPNCLIENTS
R1(config-isakmp-group)#netmask 255.255.255.0
R1(config-isakmp-group)#exit
R1(config)#crypto ipsec transform-set mytrans esp-3des esp-sha-hmac
R1(config)#crypto dynamic-map mymap 10
R1(config-crypto-map)#set transform-set mytrans
R1(config-crypto-map)#reverse-route
R1(config-crypto-map)#exit
R1(config)#crypto map mymap client authentication list VPNAUTH
R1(config)#crypto map mymap isakmp authorization list VPNAUTH
R1(config)#crypto map mymap client configuration address respond
R1(config)#crypto map mymap 10 ipsec-isakmp dynamic mymap
R1(config)#ip ssh version 1
R1(config)#spanning-tree mode pvst
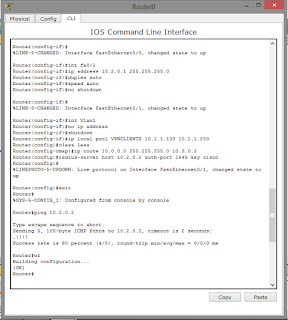
R1(config)#int fa 0/0
R1(config-if)#ip add 10.3.0.1 255.255.255.0
R1(config-if)#duplex auto
R1(config-if)#speed auto
R1(config-if)#crypto map mymap
R1(config-if)#no sh
R1(config-if)#ex
R1(config)#int fa 0/1
R1(config-if)#ip add 10.2.0.1 255.255.255.0
R1(config-if)#duplex auto
R1(config-if)#speed auto
R1(config-if)#no sh
R1(config-if)#exit
R1(config)#int vlan1
R1(config-if)#no ip add
R1(config-if)#sh
R1(config-if)#ex
R1(config)#ip local pool VPNCLIENTS 10.1.1.100 10.1.1.200
R1(config)#class less
R1(config)#ip route 10.0.0.0 255.255.255.0 10.3.0.2
R1(config)#radius-server host 10.2.0.2 auth-port 1645 key cisco
R1(config)#exit
R1#
Jika sudah selesai mulai Ping ke amalat itu sendiri jika hasil nya Pentung, maka
sudah terhubung ke server,
Ingat ! selesai konfigurasi jangan lupa simpan konfigurasi dengan ketik perintah
r1#write memory
jika ingin melihat hasil konfigurasi , maka ketik perintah
R1#sh run
R1#ping 10.2.0.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.2.0.2, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 0/0/1 ms
R1#

Untuk R2
router>en
router#conf t
router(config)#hostname R2
R2(config)#ip ssh version 1
R2(config)#spanning-tree mode pvst
R2(config)#int fa 0/0
R2(config-if)#ip add 10.3.0.2 255.255.255.0
R2(config-if)#duplex auto
R2(config-if)#speed auto
R2(config-if)#no sh
R2(config-if)#exit
R2(config)#int fa 0/1
R2(config-if)#ip add 10.0.0.1 255.255.255.0
R2(config-if)#duplex auto
R2(config-if)#speed auto
R2(config-if)#no sh
R2(config-if)#ex
R2(config)#int vlan 1
R2(config-if)#no ip add
R2(config-if)#sh
R2(config-if)#ex
R2(config)#class less
R2(config)#ip cef
R2(config)#ip route 10.2.0.0 255.255.255.0 10.3.0.1
R2(config)#ip route 10.1.0.0 255.255.255.0 10.3.0.1
R2(config)#ip route 10.1.1.0 255.255.255.0 10.3.0.1
R2(config)#ex



SETTING PC
1. PC 0.


2. PC 1.


HASIL SUKSES










Tidak ada komentar:
Posting Komentar